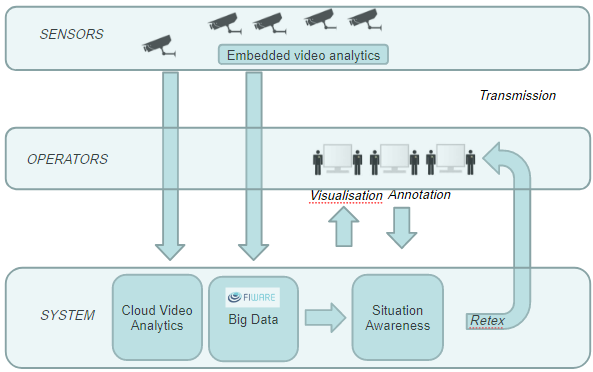
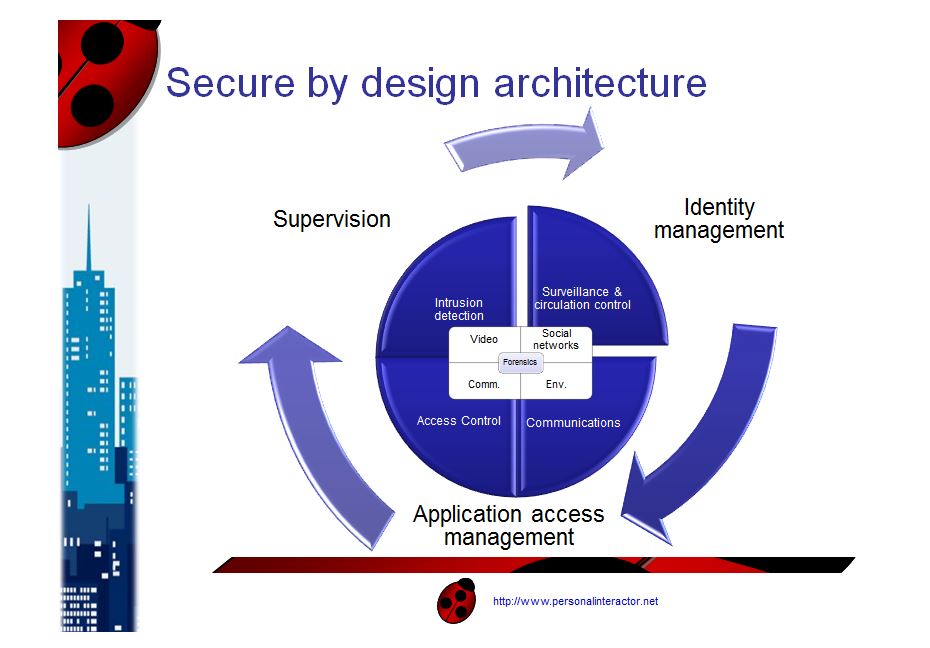
Design Thinking applied to new services in Public Safety
“We are moving to a new age of predictive policing where officers will work alongside machines to gather and analyse data to support police investigations and operations, ultimately helping to prevent and reduce crime and enhance security.” Source: http://www.eolasmagazine.ie/overcoming-public-service-challenges/ … Design Thinking applied to new services in Public SafetyLire la suite »
Design Thinking applied to new services in Public Safety Lire la suite »