The right to be secure is part of the Universal declaration of Human Rights in its article 3 :
“Everyone has the right to life, liberty and security of person.”
This notion is now bound to evolve as new threats on our lives come from the virtuality, although they impact us concretely. Not only do we need safe places to live, but also safe virtual environments to interact with. The missions of police and defense institutions are consequently due to follow and as much as possible anticipate the new threats and extend their reach to cyberdefense. That is summarized in three major new missions :
- Protect citizen privacy
- Protect city IT infrastructures
- Protect public IT services
It has been made clear in the United States Department of Homeland Security (DHS) missions that securing Cyberspace must be achieved, exactly as preventing terrorism and enhancing global security on the geographical territory. Cyberspace is indeed a new territory that needs to be defined, delimited, supervised and protected.
In effect, another mission of DHS as stated by US Government is to secure and manage borders (physical borders), which has a direct equivalent in the cyberspace, although much more difficult to define and represent. Isn’t it however mandatory to crop one’s territory to protect it.
Without borders, can’t see intruders
If difficult for a country to crop its exact digital borders, specially when global access providers distributing internet access devices all around the globe (by satellites and even in baloons), the exercise shows easier for a city, by essence located in a single geographical spot.
Yet, globalization of computing resources and cloudification of the web makes it difficult to conceive an Information System that follows the physical urban model. It seems that we need to inject some wisdom in the foolish IT jungle to tailor it to the new age security needs and manage to solve the difficult equation of joining in the same theory a perfect physical security and a non questionable logical one.
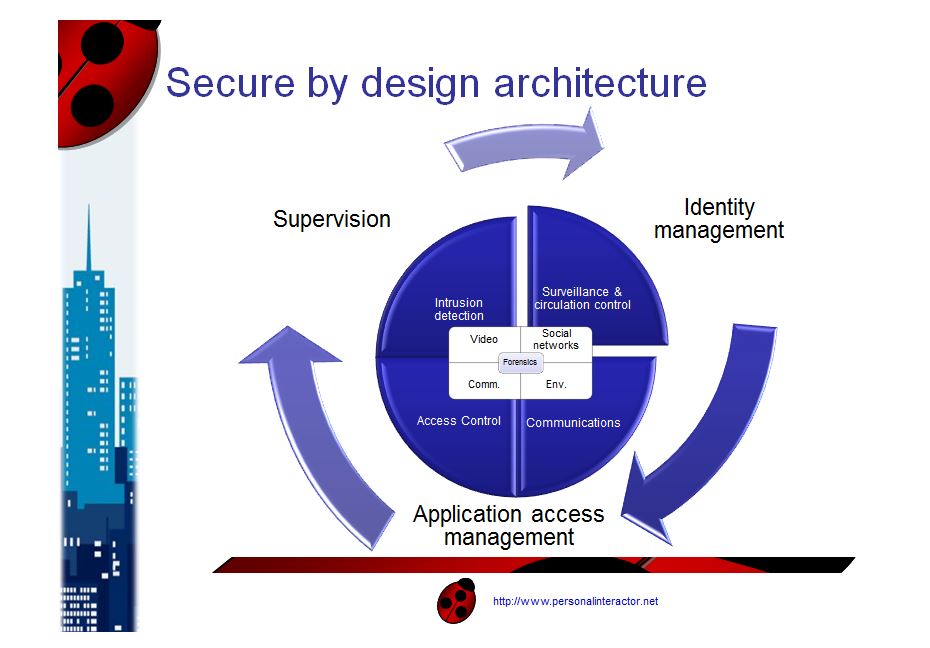
There comes the need for a strong design model, a framework gathering the efforts of the brick and mortar community, physical security, crime prevention through environmental design, and the principles of cybersecurity, cryptography and identity management.
But there is more to define than just equivalent of physical boundaries and physical identity controls. Exact replicas of many other concepts which have proven essential to the physical world, are now essential as well in the cyberworld, and cops patrols at first. Hence it is not only a question of products but also and most notably a matter of processes and actors that need to be defined, created and operated in the cyberspace if we expect that place to be as safe as the real one.
Resilience is not an option
As the institutions call on technology to supervise us, as new networks, applications and systems are used to make us more secure, it appears an uttermost emergency that urban design incorporates the same resilient views as major internet companies. As being secure is being IT dependant, it is also being energy dependant.
Smart cities, like feodal cities will have to erect physical defenses, and they will additionally have to erect virtual ones. Primarily to protect their major systems, energy sources and vital resources, these virtual fences will also protect their own security systems.
Security and privacy by design
In the race for global security, every individual represents a resource, a client but also a threat, an internal threat. Security and privacy are at both ends of the wide spectrum of services that will trade impunity against identity to eliminate the risks attached to these threats. Acceptance of this reality will materialize in smart cities under the presence of multitude of sensors that will be part of the data ecosystem and help prevent malevolence.
These sensors will generate data regarding the location, the individual behavior, the group behavior, the environment. They will include more and more video and audio data which will be massively indexed and fusionned with contextual data. In this context, miniaturization of video sensors, meshed wifi networks and technology embedded urban furnitures will play an essential role. They will take part to the massive coverage of the smart city environment by data feeds that will pose a real challenging set of questions regarding their access rights and their usage. It can be foreseen that in the light of wide adoption of social networks, data access and usage restrictions will substantially evolve. Privacy and anonimity will tend to overlap while public information meaning will be extended to whatever information is not hidden and may be used by anybody. That will particularly be true for image as access to public video feeds multiplies.
If you can be there you can see there
Private is by essence restricted in access. On the other hand, public data sometimes carries a few subtilities. As wearable, fix and vehicule operated cameras spread over our environment, it will become evident that supervizing urban environment can and must be operated in cooperation with private companies and public organizations. While far more questionable for supervsion of private and sensitive sites, private supervision makes totally sense in public environments where by essence anybody may be. Once admitted, which is still not the case in France, private companies will be entitled to join in to the urban supervision ecosystem and will take an important part of a treasure still undiscovered. As a matter of fact, failure of intelligent video analytics in replacing purely the operator leads to a complete redesign of video surveillance processes where human interpretation is key to the overall utility of the system. DARPA has understood the issues at stake and reorients its video analytics projects from alarm to text description automated generation. No doubt, video is the richest media we have and that’s why we need brains to understand it.
Your comments much awaited !